Over the past several years, traditional information governance and records management sectors have collided with the burgeoning fields of data privacy and information security, making the successful selection (and use) of enabling technologies difficult. Fortunately, there is an opportunity to use purpose-built solutions to manage data across various GRC use cases and meet the needs of the ever-expanding list of stakeholders.
Gartner’s report Beyond GDPR: Five Technologies to Borrow from Security to Operationalize Privacy (report available to Gartner subscribers) (May 6, 2019) finds the following key challenge:
“The security discipline has since long focused on enhancing control over data in general, while privacy-focusing professionals struggle to gain control specifically over personal data, though both may benefit from implementing and managing the same technology together.”
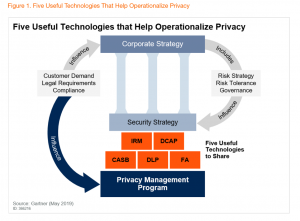
In this report, VP Analyst Bart Willemsen and Principal Analyst Zaira Pirzada do an excellent job proffering a forward-thinking operational model:
“The required tooling must span the capabilities of discovery, mapping, classification, access controls, pseudonymization or anonymization, and end-of-life controls. Integrated risk management (IRM) sets the outline of what is needed. The four other markets of cloud access security broker
(CASB), data-centric audit and protection (DCAP), data loss prevention (DLP) and file analysis (FA) bring the specific technologies to create cohesion between data security control and privacy.”
“Establish. Maintain. Evolve.”
Gartner suggests “Gaps in compliance with various regulations and standards can be assessed based on an underlying framework, as can be found in various IRM solutions.” The Gartner graphic from the report shows the framework: Establish, Maintain and Evolve (see Figure 2 below).
We believe this graphic shows that only by focusing on these discrete phases and the underlying components is it possible to determine which elements of the five interrelated technologies (Integrated Risk Management/IRM, Records Management/RM, Data-centric Audit & Protection/DCAP, Cloud Access Security Broker/CASB, Data Loss Prevention/DLP and File Analysis/FA) make the most sense for your privacy program.
Figure 2. Technology-Driven Privacy Program
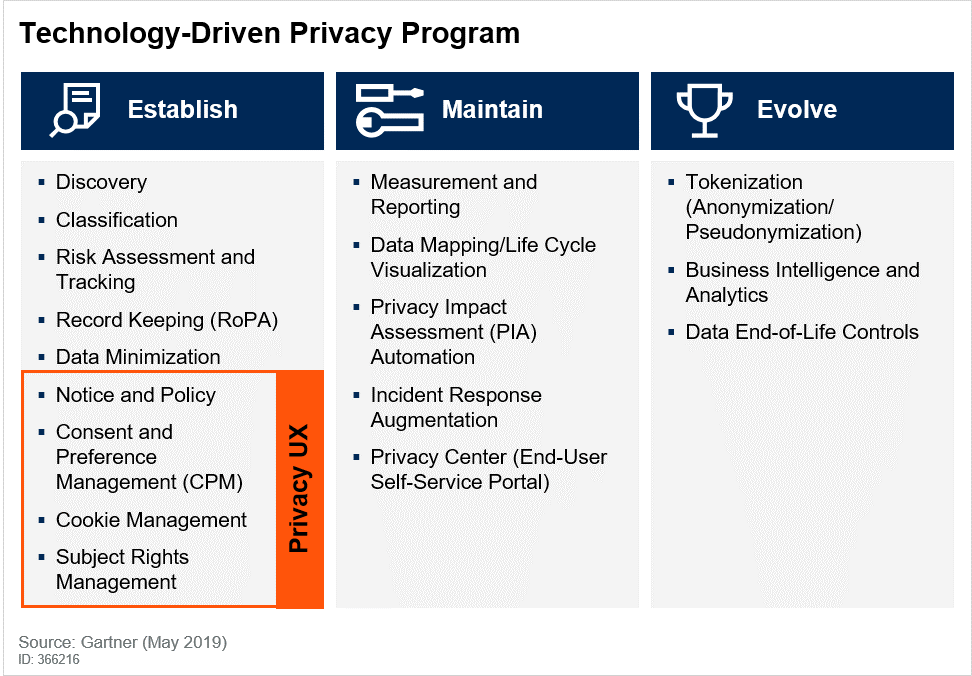
Active Navigation believes that FA solutions play a particularly critical role in the creation of a technology-driven privacy program, given its importance in the Establish phase, specifically in the initial steps of Discovery and Classification. According to the report by Gartner,
“FA tools provide a means of identifying, classifying and reporting on personal data. Most of these tools scan, map and manage unstructured data stores, and some further analyze, index, search, track and report on file metadata and content.”
Active Navigation is included in the Gartner report as a Sample Vendor for FA tools. We believe Active Navigation’s Discovery Center is well-positioned to help organizations establish a baseline program that can achieve regulatory compliance and minimize information risk. Further, we believe our Discovery Center adheres to many of the FA requirements Gartner makes in this research report:
According to Gartner: “A few vendors can do this on petabyte scales.”
- Scale
Given the need to work in the vast area of unstructured data, capability at petabyte scale is table stakes for any top-tier FA vendor. This capability is one that trips up many ancillary technologies like eDiscovery or DLP, which aren’t built to operate at this massive scale
According to Gartner: “In general, FA tools require little customization.”
- Pre-built Configuration
Out-of-the-box, Discovery Center has pre-built workflows, rule sets and taxonomies that help customers perform common tasks such as finding ROT (Redundant, Obsolete, and Trivial) data, as well as identifying sensitive/personal information. Additionally, custom workflows can be built to achieve bespoke results.
According to Gartner: “Enterprises should disregard vendors that cannot provide a complete proof of concept (POC) on a representative dataset in less than 10 days.”
- Quick Time-to-Value
Active Navigation is able to execute a 5-terabyte proof of concept in 1-3 business days. Within a week, a standard POC can be completed and the enterprise can harness the resulting metrics to drive implementation timelines and map to success criteria.
According to Gartner: “Reporting capabilities typically deliver details on (personal) data volume, age, duplication, last update and ownership.”
- Robust Reporting
Discovery Center has fully configurable reporting modules that allow insights into the discovered data and any downstream actions taken. Reporting on data is just the start, and without the ability to act on what one finds it can be a challenge to effectively realize the value of those reports. Discovery Center integrates a wide range of disposal actions directly into its reporting interface. This means that users can move easily from any report to the appropriate disposal action (including deletion or quarantine, migration or tagging in place).
As the worlds of information security and data privacy collide, it is important to utilize a “horses for courses” approach to tool selection. Each use case can and should be mapped to available technologies to ascertain the best fit. Using tools beyond their designated sweet spots will likely result in delays and disappointment.y
Interested in learning more about how Active Navigation’s Discovery Center can help your organization? Click here to schedule a demo.
